The need for improved HIPAA compliant technologies is becoming more apparent.
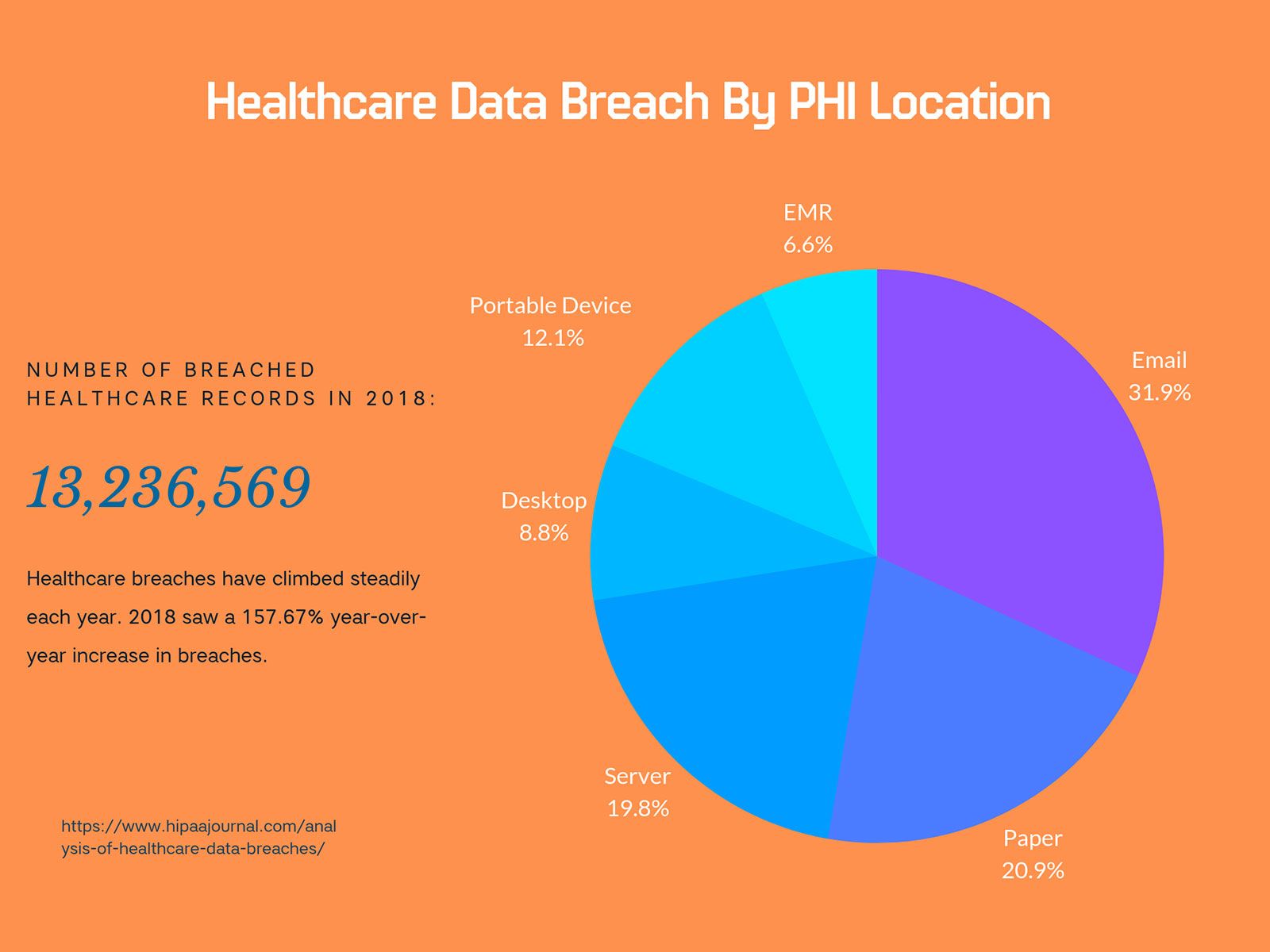
The number of data breaches in the healthcare industry has increased steadily for the past four years. From 2015 to 2018 alone, healthcare breaches increased by more than 26%. And while cyber attacks are growing across all sectors, the healthcare industry is especially vulnerable.
A recent Ponemon Institute study shows that, on average, healthcare records sell for 250% more than other information on the dark web.
These records are so valuable because of their diverse implications. Stolen healthcare records often contain financial, contact, medical, employment, and other personal identification information – like social security numbers. Cyber thieves use that information to further their criminal endeavors through fraud, identify theft, intellectual property theft, blackmail, and extortion.
And that’s really just the tip of the iceberg.
Once healthcare data gets in the wrong hands, cyber criminals can not only cause harm to the healthcare institution, but also victimize and revictimize patients – threatening to reveal compromising information or gaining access to their financial accounts.
HIPAA was implemented in 1996 to help protect patient data and safeguard medical information, but the threat landscape has changed a lot since then. Now, data breaches are less likely to occur from stolen physical records and more likely to come from cyber incidents.
For context, healthcare cyber breaches exposed the data of 22 million people this July alone.
But, “cyber breach” is a pretty broad term. What is the actual risk for healthcare institutions? When you parse down the actual causes of healthcare cyber breaches, you quickly see that there is one main culprit: email.
HIPAA Compliant – Security Rule
For the last several years, email has been the most likely cause of a healthcare cyber breach. These email incidents include phishing attacks, unauthorized email access, and misdirected emails.
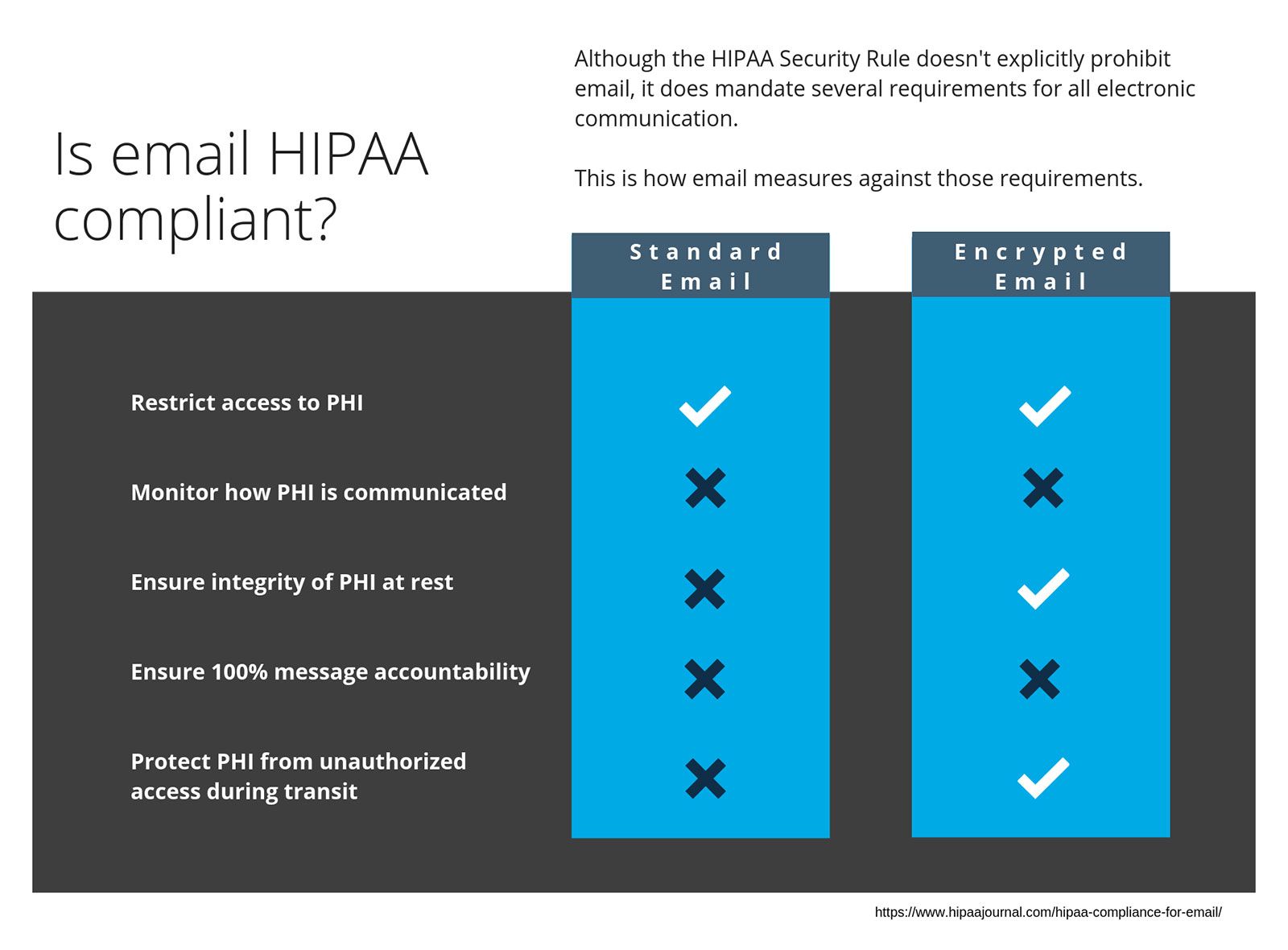
Office of Civil Rights (OCR) realized the danger of email and revised the HIPAA Security Rule to focus more intently on email communications. In that 2013 amendment, the OCR outlined new rules for HIPAA compliant email.
They include:
1) Controls restricting access to PHI
2) Audit controls to monitor how PHI is communicated
3) Controls to ensure the integrity and security of PHI at all times
4) ID authentication
5) 100% message accountability
Email doesn’t offer those security measures.
Most Common HIPAA Violations
Even though email falls short, the healthcare industry continues to rely on it as a primary source of communication.
And the result?
Here are two of the most common HIPAA violations:
1) Failure to use encryption to safeguard ePHI on portable devices
2) Email ePHI to personal email accounts
Both of these violations include email related infractions – and they come with hefty fines. In the worst cases, HIPAA violations can cost up to $1.5M per incident or exposed record.
But What About Encrypted Email?
Some healthcare institutions believe that as long as they use an email service advertised as “encrypted,” they meet the HIPAA standards.
Unfortunately, even encrypted email leaves healthcare institutions vulnerable and fails to meet the Security Rule. Not only do “secure email” services neglect the audit control or ID authentication requirements of HIPAA, many also leave glaring vulnerabilities through their encryption protocols.
Even users of ProtonMail, a popular encrypted email service, were subject to phishing attacks just two months ago.
So, what are healthcare institutions supposed to do?
According to HIPAA Journal , the answer to the healthcare industry’s email woes isn’t faulty email encryption. It’s secure messaging.
HIPAA Compliant Secure Messaging
HIPAA places so much emphasis on email compliance because email is inherently insecure. Across all industries, email is the predominant cause of data breaches – 91% of them. And, naturally, the high stakes of healthcare information lead directly to increased regulation of the mostly likely cause of a breach – email.
And this isn’t just theory. Last month, a medical group in Washington State suffered a breach that affected over 88,000 patients. The attackers held the group’s computer systems hostage while demanding a $1M ransom.
And how did they access those records? The hackers didn’t breach the network. They didn’t know someone who gave them access. All they did was send a malware infected email.
When the unsuspecting employee opened the email, the hackers used the employee’s computer to gain access to the larger group network.
HIPAA Journal points out that secure messaging overcomes issues with non-HIPAA compliant email. Secure messaging apps allow admins to monitor user activity, create audit trails, and limit message access to only authorized parties.
Additionally, secure messaging platforms generally use stronger encryption models than those found in secure email and allow for remote deletion of messages and files.
And, generally speaking, HIPAA Journal is right.
Problems with Secure Messaging
While secure messaging platforms typically bill themselves as offering high levels of safety for communications, many miss the mark.
Even for basic communications, popular messaging apps are prone to security lapses and encryption problems.
To ensure that they’re meeting the HIPAA Security Rule, healthcare institutions should ensure that their messaging service uses true end-to-end encryption. Unfortunately, most “secure” messaging apps don’t. They either unencrypt data at the server or store encryption keys on the server. These faulty encryption practices give hackers the opportunity to either intercept messages while they are unencrypted, or steal encryption keys and decrypt data.
That’s unacceptable for HIPAA compliance. Personal health information communications must be fail-proof.
Solution
So, what are health institutions to do when working diligently to ensure data security?
Email provides ease and speed in communication, but is inherently insecure – and is generally not HIPAA compliant.
Most messaging apps weren’t designed for HIPAA compliance and, therefore, fall short in meeting the requirements.
In guaranteeing security, compliance, and efficiency, HighSide is the best choice for healthcare institutions.
HighSide is the most secure unified communications and file sharing platform on the market and provides:
- True, patent-pending end-to-end encryption
- Advanced MFS (Passwordless authentication)
- Secure image capture, sharing, and storing
- Secure file transfer and storage
- Built-in message and event compliance logs
- Granular user permissions and access controls
- Geolocation-based access controls and encryption
- Alerts for announcements and emergencies
- Group and private messaging
- No encryption keys on the server
The HighSide team is also preparing to launch message delivery confirmation, secure voice and video calls, and EHR integration to further enhance secure healthcare communications.
But most importantly, HighSide was designed to meet HIPAA standards.
The platform is easy to use and encourages increased work collaboration and productivity. In fact, studies show that people are more likely to open messages more quickly as compared to email. 90% of people read messages within three minutes of receiving them, but 25% of emails remain unopened for at least 48 hours.
How would efficiency increase if everyone was reading and acting on communications within three minutes? This is especially relevant considering that a recent study by medRxiv shows that, due to communications failures, over half of healthcare institutions don’t comply with the timelines set forth in HIPAA Right of Access.
Such failures recently cost a Florida provider $85K in HIPAA violation fees.
The real tragedy is that employees at that practice didn’t even realize they were in violation of the law. HighSide removes the guesswork from HIPAA communications compliance.
Familiar Scenarios
Here’s a scenario any healthcare professional knows well…
A patient comes in to see his GP. After an evaluation, the GP refers the patient to a specialist. The GP has to send over the patient record in order to prepare the specialist, ensure the patient is receiving the necessary care, and facilitate continuity in the patient’s record.
The specialist and GP are committed to providing the most comprehensive and appropriate care, so they remain in regular contact during evaluations and treatments. After treatments are complete, the specialist updates the record and returns it to the GP.
The problem? Most of those conversations between the GP and specialist take place over email, or worse – insecure, non-HIPAA compliant messaging platforms.
With HighSide, the specialist and GP could create a channel to discuss the patient record and treatment plan. Doing so would facilitate better collaboration. It would allow healthcare professionals to more effectively treat patients while better safeguarding their PHI and meeting HIPAA requirements.
Or how about this…
A medical practice operates offices on the east and west sides of the city to better serve the community.
On Tuesdays and Thursdays, the pediatrician is at the east office. The rest of the week she works on the west side. Even when the pediatrician is off-site, nurses contact her with patient concerns and scheduling needs through text. She always has her phone with her and can respond immediately when necessary.
This system works great, right!?
Unfortunately, this common scenario is a huge violation. In the spirit of maintaining active communication and meeting patient needs, many healthcare providers resort to text messaging when a doctor or nurse is offsite. The violation is not intentional, but represents a lack of understanding of the HIPAA security requirements, the extent of what constitutes PHI, and the risk of data breaches.
HighSide would allow all members of this distributed practice to communicate securely, regardless of where they were working. The platform even takes HIPAA compliance a step farther with network and storage data loss prevention (DLP) measures that prevent unintentional information exposure and data breaches.
And with cell phones, security is left to the mercy of the service provider and device operator. HighSide overcomes those soft spots by providing intrinsic mobile device management (MDM) functionality that allows remote message deletion and geo-location restriction.
Provider-to-Patient
HighSide even provides a HIPAA compliant means to discuss sensitive information directly with patients. Though several healthcare facilities have instituted patient portals to solve the provider-to-patient communications gap, patients don’t want to use them. In fact, some estimates rate engagement through patient portals as low as 5%.
Instead of navigating through a portal and having to remember another password, patients want to communicate in a way that’s familiar, fast, and simple.
So, how do healthcare facilities communicate with patients, instead?
Many use non-HIPAA compliant, insecure methods like email or text in an attempt to meet the patient’s communication style.
But HighSide provides all the communication functionalities that patients want. It gives an interface patients are familiar with without the extra “noise” associated with patient portals. Furthermore, healthcare professionals can set user permissions to limit patient access, ensuring they are directed only to relevant message channels and files.
With HighSide’s message accountability features, healthcare institutions can streamline communication.
So, instead of fumbling with complicated, and inefficient communications platforms that don’t meet HIPAA or patient standards, the healthcare industry is best served with HighSide.
It’s the only option that was designed for HIPAA compliance and ensures PHI security while increasing efficiencies and productivity.
 Cecilia Clark
Cecilia Clark